Brought into consideration in 2010 by analyst firm Forrester Research, with vendors such as Google and Cisco, Zero Trust is primarily a strategic approach to cybersecurity that safeguards organizations from cyber threats by validating every stage of digital interaction.
Being one of the top cloud transformation service providers, Copper Mobile’s team of experts has compiled the nuances of Zero Trust Architecture and how it benefits enterprises in detail.
Continue reading to unfold one of the most discussed cyber security terms – Zero Trust Architecture.
Zero Trust Architecture – An Overview
Zero Trust Architecture is a new-age security approach that fortifies an enterprise by limiting privileged access and establishing strict identity verification and explicit permission for every person or entity trying to access the network, irrespective of whether the person is an internal part of an enterprise’s network or accessing that network remotely.
In essence, the tenet of the Zero Trust Architecture is that vulnerabilities most commonly appear when organizations trust individuals or devices, thus suggesting that instead of assuming everything is secure in the corporate firewall, enterprises should “never trust, always verify” by having multiple layers of identity, robust device authentication measures, and lateral segmentation throughout the network to mitigate the potential cyber threats & data breaches.
Also, Read – TOP 7 CYBER SECURITY THREATS & PREVENTIONS FOR ENTERPRISES
Top 5 Benefits of the Zero Trust Architecture Model for Enterprises
As read earlier, primarily Zero-Trust network model leverages identity-based authentication to form trust and allow access while keeping the IP address undisclosed.
Contrary to VPNs, Zero Trust Network Architecture – ZTNA allows access to specific applications and not the entire network on a need-only basis, thus averting lateral movement and minimizing the risk of data loss.

In addition, here are the top 5 benefits of adopting the Zero Trust Network for enterprises:
- User Experience: Zero Trust Network is essentially native to cloud environments and thus doesn’t backhaul traffic to a data center, enabling security controls to be applied in real-time while empowering the end users to seamlessly work on the most critical applications with the security Architecture.
In addition, Zero Trust Architecture enables users to seamlessly deploy single sign-on (SSO) tools that effectively simplify keeping track of multiple users and passwords.
- Scalability: Zero Trust Network Access being cloud-native, is well-equipped to autoscale across the entire organization’s network without hampering the workflow irrespective of the end user’s location or device.
- Seamless Migration of Applications & Data: When moving data and applications from private data centers to a cloud environment, or vice versa, having a Zero Trust Architecture can empower enterprises to manage the migration of data and applications centrally without struggling to recreate the security policies at every data entry point.
- Greater Visibility & Simplified IT Management: In contrast to traditional VPNs, Zero Trust Architecture enable enterprises to perpetually monitor and identify potential risks from a centralized dashboard while functioning with a complex IT ecosystem.
- Ensuring Continuous Compliance: Deploying a Zero Trust architecture creates a seamless audit trail by monitoring, evaluating, and logging every access request, thus supporting continuous compliance with audits and improving the overall speed and efficiency of upholding governance.
With that discussed, it’s easy to conclude that deploying a Zero-Trust Architecture can help enterprises cater to the modern hybrid workforce’s cloud security requirements by equipping business leaders with secure access monitoring at every layer of the organization’s network.
Core Principles of Zero Trust Architecture
By now, it’s pretty evident that Zero Trust is much more than just user identity verification, segmentation, and secure network access. It’s more of a strategy that enterprises can implement to build a more secure and beneficial cybersecurity ecosystem.
To help you better understand the essence of Zero Trust Architecture, here are the core principles of the modern security Architecture that enterprises are rapidly moving towards.
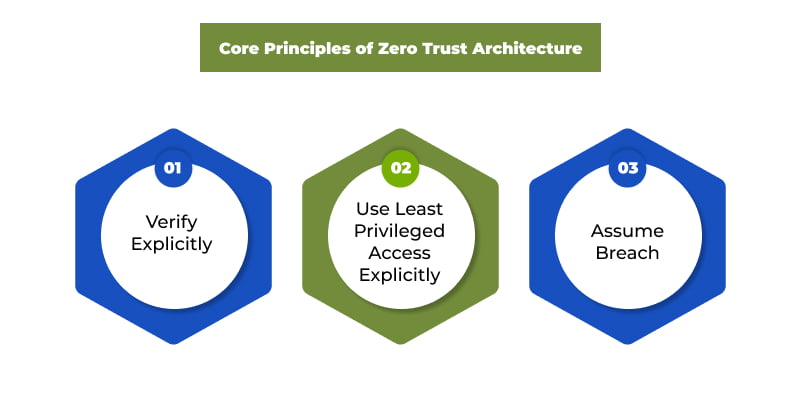
#1 – Verify Explicitly
As the prime precept of Zero Trust Architecture is to “never trust and always verify,” the first core principle signifies the importance of continually monitoring, verifying, authenticating, and authorizing network access for all available data points, be it user identity, location, device usage, data classification, service, and anomalies.
#2 – Use Least Privileged Access
Another fundamental principle of the Zero Trust security Architecture mandates restricting privileged user access based on roles and needs while introducing risk-based adaptive policies and data protection criteria to help secure data and enhance productivity.
#3 – Assume Breach
The third core principle of Zero Trust Architecture is to minimize blast radius, i.e., the reach that a faulty configuration change might cause and segment user access. In addition, verify end-to-end encryption and analytics to gain visibility, drive threat detection, and improve defenses.
Also, Read – MOBILE APP SECURITY: A COMPREHENSIVE GUIDE TO SECURE YOUR APPS
How Does Zero Trust Security Work?
At the crux, Zero Trust Network Architecture primarily focuses on granular application-level access policies that deny all users and devices default network access. Once a Zero Trust Architecture is employed every time a user connects, the Zero Trust Controller checks & verifies the device attributes until met before granting access to specific network resources or applications based upon the user’s identity and device status.
As Zero Trust Architecture ensures inaccessibility of data and resources, to deploy an efficient Zero Trust Architecture, an enterprise has to lay down a well-planned strategy and roadmap to implement and integrate robust security tools that help achieve business-focused outcomes.
Deploying a Zero Trust Architecture? Here’s What You Need to Do:
- Deploy secure access service edge (SASE)
- Utilize micro-segmentation & fragment security perimeters into smaller zones
- Use Multi-Factor Authentication (MFA) to assign user access based on roles
- Restrict privileged access & mitigate common vulnerabilities.
- Adopt a data-centric approach & validate every entry point
- Segregate and fortify workloads during cloud server cross-movement
Walking through the essence of implementing a Zero Trust Security Architecture might appear like a restrictive process. But a well-strategized deployment of a Zero-Trust model can help enterprises bring context to the rapidly evolving attack surface and improve the users’ experience.
Also, Read – WHY SHOULD YOU CARE ABOUT AWS COST OPTIMIZATION METHODS?
Zero Trust Architecture – A Necessity for Enterprises & Competitive Edge
With the accelerating need for global collaboration and the acceptance of hybrid working models and cloud solutions by the majority of enterprises worldwide, there’s a significant increase in the adoption of remote technologies with greater cyber vulnerabilities, which has made it imperative for business leaders to stay on top of the cyber requirements and adopt scalable cyber security infrastructure that helps them enhance their IT infrastructure and mitigate cyber security risks.
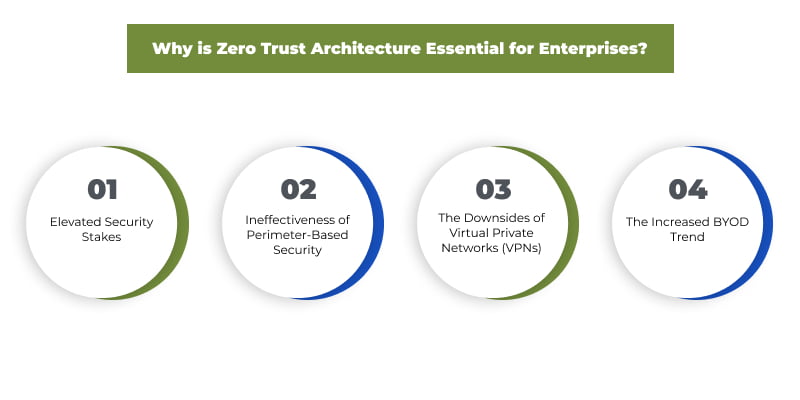
Further, here are the key reasons businesses should turn towards Zero Trust Architecture:
- Elevated Security Stakes
The modern evolution of business and its operations have also evolved the cybercriminals’ ways of disrupting the cyber infrastructure of enterprises.
Cybercriminals have begun targetting user & customer data, core business financial data, IP, and proprietary functions, leaving behind the regular DDoS attacks, which has led to an accentuated need for a robust and resilient cybersecurity strategy.
Adopting a modern cybersecurity framework – Zero Trust Architecture, will not only improve cyberinfrastructure but also enhance the cyber resilience of businesses, enabling the right mitigation strategy in case of a cyber breach.
- Ineffectiveness of Perimeter-Based Security
The constant adoption of digital technologies by businesses has made traditional perimeter-based cybersecurity models ineffective and irrelevant when defining the scope of security enforcement at an ever-quickening pace, thus leading to the increased need to monitor, authenticate and approve access privileges at every point within a network by adopting the modern cybersecurity approach – Zero Trust Architecture and eliminating unrestricted access to the system.
- The Downsides of Virtual Private Networks (VPNs)
Numerous businesses have responded to the accelerating network security complexities by deploying VPNs as their solution of choice. However, at a glance, with modern technologies, vulnerabilities, and increasing cyber security threats, enterprises need to evaluate and introduce a more thoughtful yet comprehensive approach to network access. As a result, VPNs are simply deficient in mitigating the enterprise’s modern cyber security needs.
Why are traditional VPNs insufficient? Here’s an answer to it:
- Scalability: Traditional VPNs can create bottlenecks with larger teams when delivering applications and hamper the end-user experience and productivity.
- Complexity: Deploying a VPN can be a complicated configuration process resulting in too much time consumption and ineffective user management.
- Vulnerability: Traditional VPNs often cannot detect risk, thus, leading to an increased risk of compromised credentials and data misuse.
- Visibility: VPNs being perimeter-focused, only controls access at the network level, which leaves the external application layer more vulnerable and prone to attack.
- Privacy: When an enterprise deploys and connects to a VPN server, all the user traffic is backhauled to the central data center, thus compromising data protection & privacy.
- The Increased BYOD Trend
With the new hybrid working model, workers are often asked to work on their devices, which are more prone to cyber-attacks and lack basic cyber hygiene skills.
Introducing a Zero Trust Security Architecture can help enterprises effectively manage and monitor network access while mitigating the potential security breach following the fundamental “trust nobody; verify everything” rule restricting access controls at each level within the network.
With that read, it’s easy to conclude why organizations are turning towards alternate solutions.
For instance, a recent report by Gartner has revealed a massive shift of 60 percent of enterprises to Zero-Trust network access (ZTNA) by 2023, abandoning the traditional VPNs.
Also, Read – A GUIDE TO ONLINE PRIVACY, SECURITY, AND PEACE OF MIND
With all of the discussed, it’s easy to conclude that the Zero Trust Security model is needed with the ever-changing business technologies and increased cyber vulnerabilities. Therefore, to ensure a more substantial IT infrastructure, businesses must be proactive in introducing the new age cyber security approach – the Zero Trust Security framework providing network visibility, consistent monitoring, and authentication of access to the network.
As for businesses looking for the top AWS network consulting partners, your best way is to get in touch with cloud experts at Copper Mobile, offering the most competent AWS database migration services reciprocating robust IT infrastructure, operational efficiency, and high business impact.




